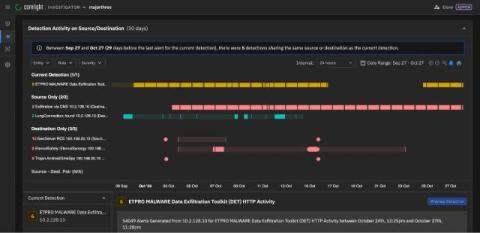
Cooking up a year of faster, smarter, and tastier security
If there’s one thing I love more than delivering great products, it’s delivering great food. The holidays are my time to channel my inner celebrity chef: I’ll burn a few cookies, over-spice a roast, and then miraculously pull it all together for a meal that leaves everyone asking for seconds (or at least not asking for the takeout menu).