Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
Devo Exchange: Use Cases & Data
Coffee Talk with SURGe: EU Data, Vice Society Ransomware, Killnet, Cybersecurity Awareness Month
Deliver a Strike by Reversing a Badger: Brute Ratel Detection and Analysis
A new adversary simulation tool is steadily growing in the ranks of popularity among red teamers and most recently adversaries. Brute Ratel states on its website that it "is the most advanced Red Team & Adversary Simulation Software in the current C2 Market." Many of these products are marketed to assist blue teams in validating detection, prevention, and gaps of coverage.
Zero Day Exploit for MS Exchange (ProxyNotShell)
On Sept. 29th 2022, cybersecurity organization GTSC publicized a report outlining attacks they have seen in the wild targeting as-yet unpatched vulnerabilities in Microsoft Exchange. When successfully exploited this combination of vulnerabilities results in an authenticated Remote Code Execution (RCE) attack. Until a patch has been issued, Microsoft has posted a security bulletin detailing a workaround.
Machine Learning in Security: NLP Based Risky SPL Detection with a Pre-trained Model
The Splunk Vulnerability Disclosure SVD-2022-0604 published the existence of an attack where the dashboards in certain Splunk Cloud Platform and Splunk Enterprise versions may let an attacker inject risky search commands into a form token.
Coffee Talk with SURGe: Ukraine War, GRU Hactivist Coordination, Network Monitoring, Optus Breach
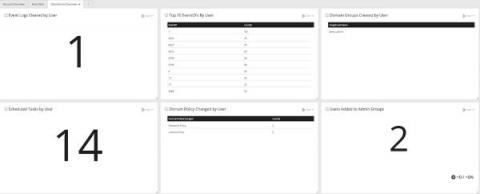
60 Second Charity Challenge: Domain Shadowing
Top Cybersecurity Frameworks Today (And How To Choose)
With the easy availability of tools and knowledge, cyberattacks have run rampant, putting pressure on organizations to better defend themselves. Security is a continuous process that grows over time — exactly why organizations need to create a strong foundation. Two important questions every organization has asked themselves: Where do we start, and have we done enough?
Cyber Hygiene: Concepts and Best Practices for Cybersecurity
Cyber hygiene has become a highly visible topic in all business segments. Creating software and new features happens at a very fast pace — requiring lots of internal processes and operations to keep this up to date. However, it's also very important to be concerned with the fundamentals of information security in order to keep the company's digital assets protected. In this post, we'll discuss in detail the concept of cyber hygiene and some good practices to follow.