Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
Data access in Multitenancy
Defense Department's Multi-Cloud Cloud Strategy: A Role for SIEM
It’s difficult to recall a time over the last ten years when cloud requirements were not at the forefront of the Defense Department’s modernization efforts. Cloud capability reviews and requirements, in some form, extend from the Pentagon’s net-centricy efforts — to the Joint Information Environment, Digital Modernization, and up through to today.
Coffee Talk with SURGe: Twitter Whistleblower, Roasting Oktapus, Montenegro Cyberattack
Introduction to Splunk Common Information Model
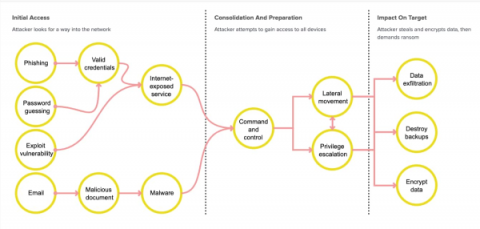
AppLocker Rules as Defense Evasion: Complete Analysis
Microsoft continues to develop, update and improve features to monitor and prevent the execution of malicious code on the Windows opearting system. One of these features is AppLocker. This feature advances the functionality of software restriction policies and enables administrators to create rules to allow or deny applications from running based on their unique identities (e.g., files) and to specify which users or groups can run those applications.
Announcing: Code-free API log collection and parser creation
AT&T Cybersecurity is pleased to announce a code-free way for our USM Anywhere customers to make their own API-driven log collectors and custom parsers. This big advancement in threat detection and response technology will make it possible for customers to collect information from a much larger variety of sources and SaaS services without having to request new integrations or log parsers.
Introducing the Ransomware Content Browser
Splunk SURGe recently released a whitepaper, blog and video that outline the encryption speeds of 10 different ransomware families. The outcome of this research was that it is unlikely that a defender will be able to do anything once the encryption has started. Ransomware today is also mostly “human-operated” where many systems are sought out and compromised before any encryption activities occur and, once they do, the encryption is just too fast to meaningfully affect the damage done.