Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
Quick and easy vulnerability management with Calico Cloud
As more enterprises adopt containers, microservices, and Kubernetes for their cloud-native applications, they need to be aware of the vulnerabilities in container images during build and runtime that can be exploited. In this blog, I will demonstrate how you can implement vulnerability management in CI/CD pipelines, perform image assurance during build time, and enforce runtime threat defense to protect your workloads from security threats.
Securing PHP containers
According to Wappalyzer, PHP powers over twelve million websites. Not bad for a 28-year-old language! Despite its age, PHP has kept up with modern development practices. With support for type declarations and excellent frameworks like Laravel and Symfony, PHP is still a great way to develop web apps. PHP works well in containerized environments. With an official image available on Docker Hub, developers know they can access well-tested PHP container images to build on.
What You Need to Know About Fine-Grained vs. Coarse-Grained Authorization
With the growing importance of cloud-native security and zero-trust approaches to software, questions around the level of access granted to cloud resources have become more critical. Equally important is to understand the value of different authorization strategies. In this article, we present an overview of fine-grained and coarse-grained authorization methods.
Using XACML with OPA and Rego: The Best of Both Worlds
XACML is an OASIS standard for implementing declarative authorization policy. It was intended to be a widely adopted technology that would move authorization policy decisions out of application code and into a specialized Policy Decision Point (PDP). The terms often used in the OPA world, such as PDP, PIP (Policy Information Point) and PEP (Policy Enforcement Point) all come from the XACML standard. You can read more about XACML in Anders Ecknert’s blog post on architecting authorization.
The Developer's Guide to a Seamless Kubernetes Deployment
To grasp the concept of a Kubernetes Deployment and Kubernetes Deployment strategy, let’s begin by explaining the two different meanings of the term “deployment” in a Kubernetes environment: Kubernetes Deployment allows you to make declarative updates for pods and ReplicaSets. You can define a desired state and the Deployment Controller will continuously deploy new pod instances to change the current state to the desired state at a controlled rate.
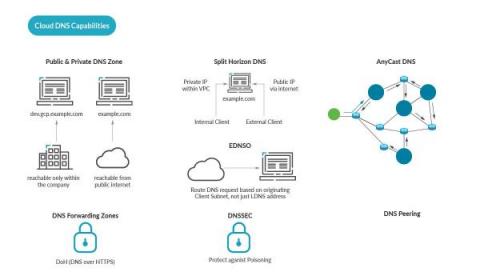
Cloud DNS Security - How to protect DNS in the Cloud
When using DNS in the Cloud, security cannot be forgotten. This article is for cloud architects and security practitioners who would like to learn more about deployment options to DNS security and security best practices for DNS in the Cloud. You will learn DNS best practices for DNS security, and see the advantages of a cloud approach for DNS. The three main requirements for DNS are: In this article, we begin with DNS basics, then move on to the topic of DNS in the Cloud.
Automating Azure Files Restore in Azure Kubernetes Service
If you are considering Azure Files as the persistent storage for your Azure Kubernetes Service (AKS) applications, there are important considerations around AKS backup and recovery with implications on how you can perform Dev, Test, and Staging. This article outlines these data management considerations in detail and how to work around Azure Files limitation to achieve feature parity with using Azure Managed Disks.
How to apply security at the source using GitOps
If your GitOps deployment model has security issues (for example, a misconfigured permission because of a typo), this will be propagated until it is hopefully discovered at runtime, where most of the security events are scanned or found. What if you can fix potential security issues in your infrastructure at the source? Let’s start with the basics.
Hunting malware with Amazon GuardDuty and Sysdig
With the constant threat of malware weighing on cloud teams, AWS is introducing new ways to identify malicious software with Amazon GuardDuty. Amazon GuardDuty Malware Protection, a fully managed malware detection service launched today at Re:inforce by AWS, provides agentless scanning to identify when suspicious activity occurs.