Proactive Strategies to Prevent Ransomware Attacks
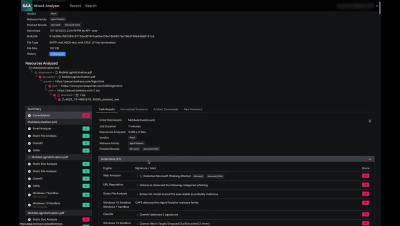
In today’s digital age, ransomware attacks have emerged as one of the most formidable threats to organizations worldwide. These malicious software attacks encrypt files on a device, rendering them inaccessible to users, and demand a ransom for decryption keys. The impact of ransomware can be devastating, leading to significant financial losses, operational downtime, and reputational damage.