Create a Custom Policy in the Veracode Platform
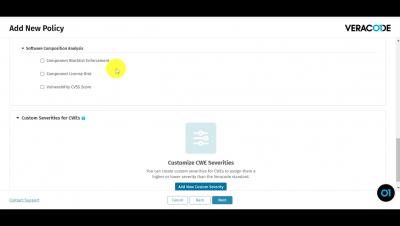
In this video, you will learn how to create a custom policy in the Veracode Platform. The Veracode Platform enables you to create an application security policy against which you can evaluate and measure your applications. You can create, edit, or delete a policy. You must have the Policy Administrator role to perform policy maintenance activities. Policies can comprise one or more of the following types of requirements for your applications: rules, scan requirements, and remediation grace periods. You define the requirements while creating a new policy.