Part 1: How Egnyte Built its Turnkey Retrieval Augmented Generation Solution
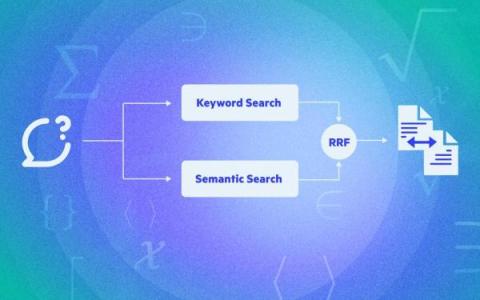
The Egnyte platform houses a lot of data. To enable users to make the most of this asset, we need to help them efficiently retrieve information. Traditional search interfaces do a decent job of retrieving information directly related to query keywords, often presenting results in a list format without additional interpretation or synthesis.