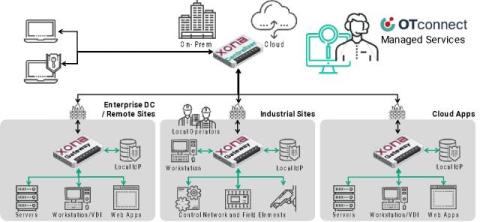
Key Steps to Achieving XDR Maturity with Microsoft (+ Free Self-Assessment Tool)
Organizations are under constant pressure to ensure that their security defenses adapt effectively to evolving threat actor methodologies. Extended detection and response (XDR) has the potential to significantly advance these efforts thanks to its ability to accelerate and streamline investigation, threat hunting and response. However, successfully adopting XDR to achieve comprehensive visibility demands some important considerations.