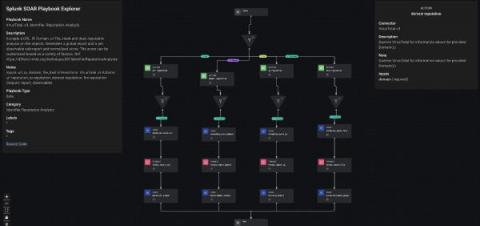
XDR vs SOAR: comparing functionalities for MSPs
Managed service providers (MSPs) must be prepared to defend their customers against advanced threats and, to do so, they need to keep track of different data sources by deploying solutions that are designed to improve their customers’ security posture through effective detection and proactive responses to potential incidents.