Securing DoD Systems - A Look at SOAR
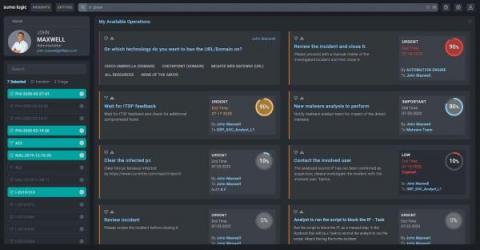
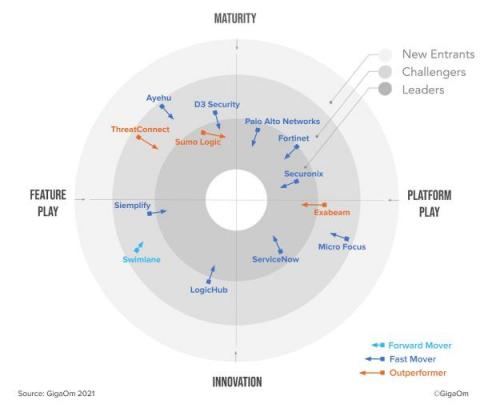
It would be hard to overstate the critical importance of security orchestration, automation and response (SOAR) capabilities for the effective mission success of security operations centers (SOC). Without a solid SOAR capability in place, an SOC will be easily overwhelmed with routine and repetitive tasks that in and of themselves could become a vulnerability.