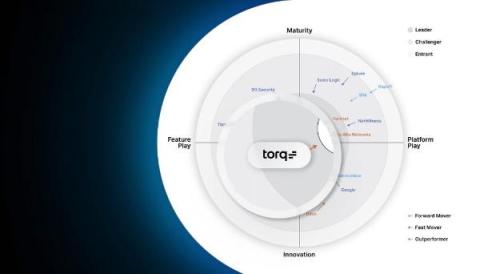
8 ways MSSPs gain competitive advantage with the SecOps Cloud Platform
Earlier this year, we introduced the LimaCharlie SecOps Cloud Platform (SCP). The SCP is a unified platform for modern cybersecurity operations. Similar to what the public cloud did for IT, the SCP offers security teams core cybersecurity capabilities and infrastructure: on-demand, pay-per-use, and API-first. In short, the SCP is a new paradigm for cybersecurity. It’s a game-changer for enterprise security teams and cybersecurity solutions builders.