Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
NetMotion by Absolute Appoints Cloud Distribution as UK Distributor for new Two-Tier Channel
The meaning behind XDR: A beginner's guide to extended detection and response
In the world of threat detection and response, alert fatigue and tool sprawl are real problems. Security professionals are struggling to manage different tools and control points and still relying on manual processes, which results in security that is fragmented and reactive. Analysts need better visibility and control, more context, and better use of automation so they can cut through the noise and respond to threats faster and more effectively.
Former Symantec and Malwarebytes Executive Joins Corelight as Senior Vice President of Product
Corelight Secures $75 Million in Series D Funding Led by Energy Impact Partners with Participation from H.I.G. Growth Partners, CrowdStrike and Capital One Ventures
4 Differences Between Threat Hunting vs. Threat Detection
Increasingly, companies are becoming aware of the importance of building threat detection and hunting capabilities that avoid putting their businesses at risk. Now more than ever, when it comes to both protecting enterprise cybersecurity and delivering effective IT security solutions and services, organizations and MSPs can no longer simply act when cyberattacks occur, but long before they even pose a threat.
Detection and response for the actively exploited ProxyShell vulnerabilities
On August 21, 2021, the Cybersecurity and Infrastructure Security Agency (CISA) released an urgent notice related to the exploitation of ProxyShell vulnerabilities ( CVE-2021-31207 , CVE-2021-34473 , CVE-2021-34523 ). By chaining these vulnerabilities together, threat actors are compromising unpatched Microsoft Exchange servers and gaining footholds into enterprise networks.
Tessian partners with Optiv Security as part of the company's move to a 100% channel model
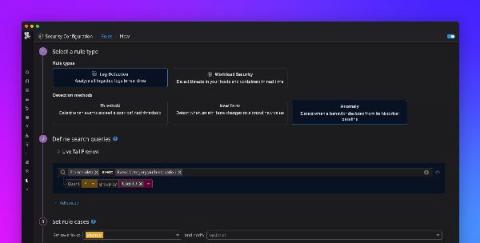
Detect security threats with anomaly detection rules
Securing your environment requires being able to quickly detect abnormal activity that could represent a threat. But today’s modern cloud infrastructure is large, complex, and can generate vast volumes of logs. This makes it difficult to determine what activity is normal and harder to identify anomalous behavior. Now, in addition to threshold and new term –based Threat Detection Rules , Datadog Security Monitoring provides the ability to create anomaly
Why social graphs won't save you from account takeover attacks
Account takeover (ATO) is a dangerous form of business email compromise (BEC). Attackers gain access to a legitimate email account within an organisation, often by stealing credentials through spear phishing. They’ll then send emails from the compromised account with the goal of getting a fraudulent payment authorised or accessing sensitive data to exfiltrate.