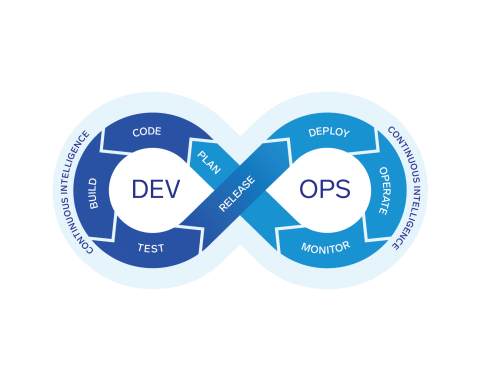
Enabling DevSecOps with the Elastic Stack
Software development and delivery is an ever-changing landscape. Writing software was once an art form all its own, where you could write and deploy machine code with singleness of purpose and no concern for things like connecting to other computers. But as the world and the variety of systems that software supports became more complex, so did the ecosystem supporting software development.