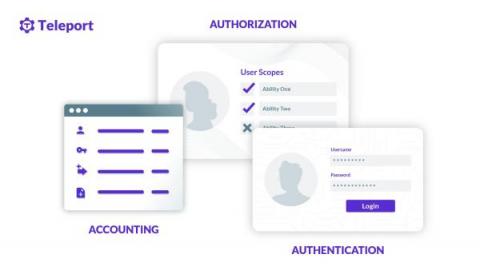
SAST vs. SCA: 7 Key Differences
Everybody’s talking about securing the DevOps pipeline and shifting security left.. AppSec tools like SAST (Static Application Security Testing), DAST (Dynamic Application Security Testing), and others that address issues in proprietary software have become staples of the developer’s security toolbox.