Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Build a software bill of materials (SBOM) for open source supply chain security
More than ever, developers are building web applications on the foundations of open source software libraries. However, while those libraries make up the software bill of materials (SBOM) components inventory, not all developers and business stakeholders understand the significant impact on open source supply chain security that stems from including 3rd party libraries.
SSH into Docker Container or Use Docker Exec?
SSH has always been the default mechanism to get remote shell access into a running Unix or Linux operating system from a terminal client to execute commands. While SSH is familiar, Docker provides more lightweight and easier-to-use methods that don’t require running your container with an SSH server. This post will explore two methods to get shell access into a Docker container using OpenSSH and the docker exec command.
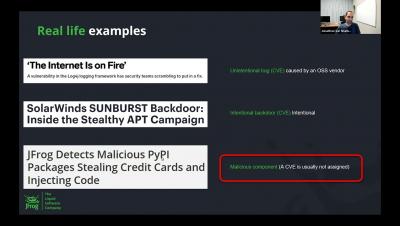
Identifying and Avoiding Malicious Packages
Artifactory Integration - Plugin Upgrade
Announcing Snyk free security for open source projects
DevSecOps Automation: How Does it Help?
DevSecOps is a key component in companies’ efforts to build strong security into the software products they create. The methodology brings together security and development teams in a joint mission to deliver high-quality, reliable and secure software.
Log4j Webinar Recap: What Your Scanner is Missing
Log4j continues to be a thorn in the side of security leaders, who have spent the last several months battling the recently discovered flaw in Apache’s Log4j software. In a recent webinar, Yotam Perkal, director of vulnerability research at Rezilion, said the implications of the bug are far-reaching and will likely be exploited for years to come. Apache Log4j is an open source Java logging library used in millions of Java applications worldwide.
Dirty Pipe - What You Need to Know
The new serious Linux Kernel vulnerability dubbed ‘Dirty Pipe’, due to its similarity to the 2016 high severity and easy to exploit DirtyCow vulnerability, was originally disclosed on March 7th by Max Kellermann. Kellermann found the bug accidently while researching corrupted log files on a log server.
Why Single Sign On Sucks
A month ago I tweeted about my annoyance with SSO or Single Sign On. While single is in the name, I’m required to “single sign on” multiple times a day. I’m not the only one; the tweet went viral with over 25k likes and 2 Million impressions. The tongue-in-check tweet created a lot of fun responses and more rage against SSO user experience than I expected. SSO was meant to solve password fatigue but we got something worse.