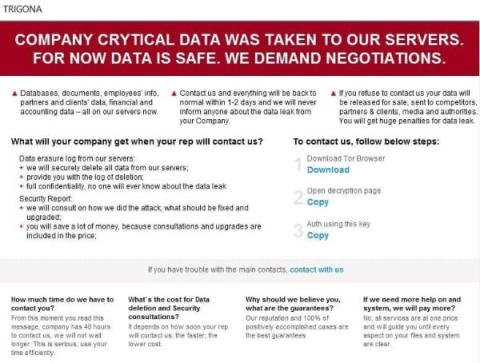
RaaS attacks are on the rise: Top 5 tips to protect your organization
Over the years, we have seen a substantial amount of cyberattacks happening around the globe. The most infamous of them is the RaaS attack, which is taking over organizations of all sizes. An employee’s sheer negligence and lack of cybersecurity solutions put organizations at higher risk. In this article, we will share some tips that every organization needs to know in order to stay away from cyberattacks. Ransomware attacks have become prevalent in recent years and can happen to any organization.