Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
January 2022
Elevate AWS threat detection with Stratus Red Team
A core challenge for threat detection engineering is reproducing common attacker behavior. Several open source and commercial projects exist for traditional endpoint and on-premise security, but there is a clear need for a cloud-native tool built with cloud providers and infrastructure in mind. To meet this growing demand, we’re happy to announce Stratus Red Team, an open source project created to emulate common attack techniques directly in your cloud environment.
Datadog Cloud Security Platform
Detectify, an ethical hacker powered EASM solution.
Cybersecurity Partners for NHS Trusts: Graylog + ANSecurity
Introducing wachy: A New Approach to Performance Debugging
Wachy is a new Linux performance debugging tool that Rubrik recently released as open source. It enables interesting new ways of understanding performance by tracing arbitrary compiled binaries and functions with no code changes. This blog post briefly outlines various performance debugging tools that we commonly use, and the advantages and disadvantages of each. Then, we discuss why and how we built wachy.
Monitoring Endpoint Logs for Stronger Security
The massive shift to remote work makes managing endpoint security more critical and challenging. Yes, people were already using their own devices for work. However, the rise in phishing attacks during the COVID pandemic shows that all endpoint devices are at a higher risk than before. Plus, more companies are moving toward zero-trust security models. For a successful implementation, you need to secure your endpoints.
Distributed Tracing with Datadog
Here at Nightfall we ensure that we are always using the most appropriate technology and tools while building services. Our architecture involves serverless functions, relational and NoSQL databases, Redis caches, Kafka and microservices written in Golang and deployed in a Kubernetes cluster. To effectively monitor and easily troubleshoot our services, we use distributed tracing across our services.
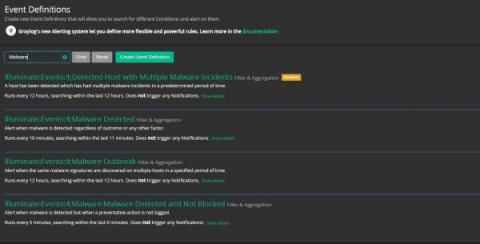
V2 Illuminate Install
Building Resilience to Financial Crime: the Convergence of Cyber Intelligence, AML, and Fraud Prevention
The idea of converging cyber intelligence, AML, and fraud prevention activities to eliminate the gaps between these silos of financial crime risk management has been discussed for years. However, recent developments in global real-time payments, open banking, and booming digital transactions have escalated the need for this convergence. In this era of instant payments and CNP transactions, traditional siloed approaches to financial crime prevention are loosing their effectiveness.
What Is FIM (File Integrity Monitoring)?
Change is prolific in organizations’ IT environments. Hardware assets change. Software programs change. Configuration states change. Some of these modifications are authorized insofar as they occur during an organization’s regular patching cycle, while others cause concern by popping up unexpectedly. Organizations commonly respond to this dynamism by investing in asset discovery and secure configuration management (SCM).
Why cloud native requires a holistic approach to security and observability
Like any great technology, the interest in and adoption of Kubernetes (an excellent way to orchestrate your workloads, by the way) took off as cloud native and containerization grew in popularity. With that came a lot of confusion. Everyone was using Kubernetes to move their workloads, but as they went through their journey to deployment, they weren’t thinking about security until they got to production.