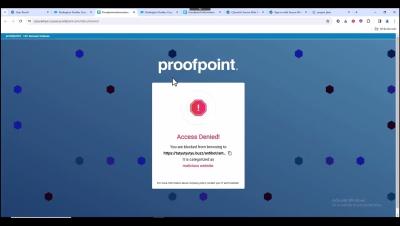
Protect Your Digital World with CyberArk and Proofpoint Browser Security!
In this video, we dive into the powerful combination of CyberArk and Proofpoint Browser Security, two leading solutions in the realm of cybersecurity. Learn how these tools can fortify your defenses against cyber threats and safeguard your sensitive information. Topics Covered: Who Should Watch: Stay Connected: Don't forget to subscribe to our channel for more insights into the latest cybersecurity trends and solutions. Hit the bell icon to get notified whenever we upload a new video!