The Secret's Out: Researchers Reveal Backdoor in Emergency Radio Encryption
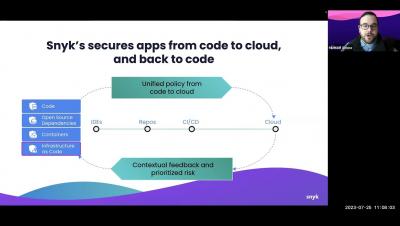
For over 25 years, a technology utilized for vital data and voice radio communications globally has remained under wraps, preventing in-depth testing for potential vulnerabilities. However, a small group of researchers in the Netherlands has now shed light on it, uncovering significant flaws, including a deliberate backdoor.