Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Serverless vs Cloud vs On-prem
Server architecture can differ in a lot of ways, but the three main categories would be on-prem, cloud and serverless. Some believe that cloud and serverless can be used interchangeably, which is not the case. To help clear up some confusion, this blog post will explain each of them and how it affects the security work.
Machine data processing and 5G, IoT, and AI at Mobile World Congress 2019
One thing that’s become evident to me after years attending Mobile World Congress is that, in fact, there are several events running in parallel, with a few common denominators: network technology providers, device manufacturers, telecom operators, and services companies all come to Barcelona to present and demonstrate the latest and greatest of the year’s dominating trends.
Internet of Termites
Termite is a tool used to connect together chains of machines on a network. You can run Termite on a surprising number of platforms including mobile devices, routers, servers and desktops. That means it can be used used to bounce a connection between multiple machines, to maintain a connection that otherwise wouldn’t be possible.
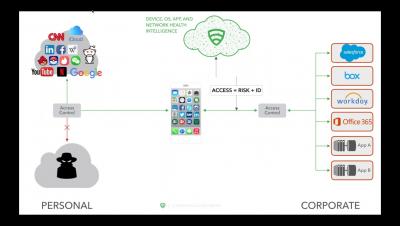
Post-perimeter security 101: Dawn of a borderless world
A Multi-Million Dollar Commitment to Our Multi-Cloud Strategy
Every business today is growing in their own unique way. Their infrastructure is made up of a combination of cloud and on-premises repositories. Their application suite is custom built with a myriad of productivity applications like Slack, Office 365, Zoom, and more. And finally, their users are working on a wide range of devices, from Apple iPhones to Microsoft Surface Pros. The common theme amongst businesses is their need for flexibility.
Securing GCP: Top 10 Mistakes to Avoid
Smart Cloud Sessions: Protecting sensitive data in Public Cloud Infrastructure
AWS System Manager And The Dangers of Default Permissions
In September of 2018, Amazon Web Services (AWS) announced the addition of the Session Manager to the AWS Systems Manager. The session manager enables shell or remote desktop level access to your AWS EC2 Windows and Linux instances, along with other benefits. This is a great new feature, but care should be taken when enabling this capability.
8 Cloud Security Best Practice Fundamentals for Microsoft Azure
In a previous blog, I discussed securing AWS management configurations by combating six common threats with a focus on using both the Center for Internet Security (CIS) Amazon Web Services Foundations benchmark policy along with general security best practices.