Sysdig Enriched Process Trees, an Innovative Approach to Threat Detection
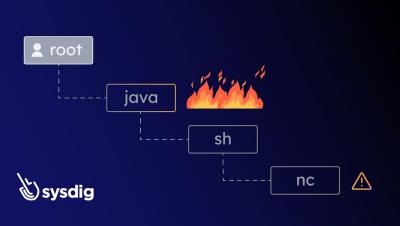
Discover how Sysdig Secure’s new Process Tree feature improves threat investigation. In order to speed up the investigation of security events, Sysdig Secure now includes a process tree showing the attack journey from user to process, including process lineage, container and host information, malicious user details, and impact. In Linux systems, a process tree refers to the hierarchical representation of running processes on a system. It depicts the parent-child relationship between processes all the way to the root.