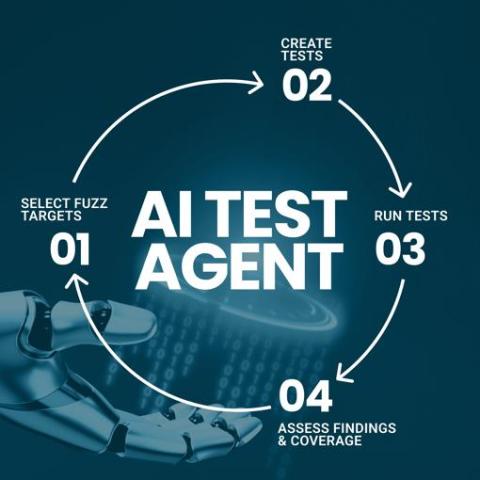
Meet Spark, an AI Test Agent That Autonomously Uncovers Vulnerabilities
We’re thrilled to announce the general availability of Spark, an AI Test Agent that lowers the entry barrier to white-box fuzz testing. In this blog, we explain how Spark works and share the main results from its beta testing that prove its effectiveness.