How to generate a Software Bill of Materials (SBOM) using Veracode Software Composition Analysis
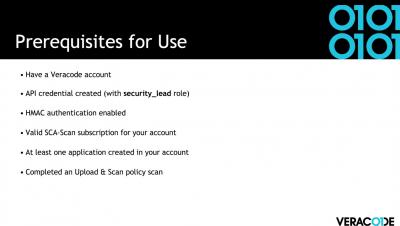
In this video, we’ll demo how to use the SBOM API with Veracode Software Composition Analysis (SCA) to generate a Software Bill of Materials (SBOM). The new SBOM API provides an inventory of components within your application with insight into the relationships between the components. Exported in CycloneDX format, the SBOM identifies which components are coming from 3rd party sources and offers visibility into your software supply chain.