FINMA Compliance: DevSecOps Strategies for Securing the Swiss Financial Ecosystem
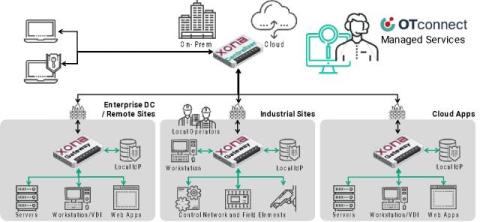
The Swiss Financial Market Supervisory Authority (FINMA) sets strict requirements to ensure that financial institutions operating in Switzerland maintain robust security and operational resilience. FINMA’s guidelines are crucial for protecting sensitive financial data, minimizing risks, and maintaining trust in the Swiss financial ecosystem. As part of that, software supply chain security plays an essential role in meeting these compliance requirements.