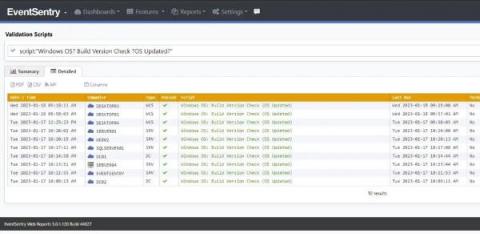
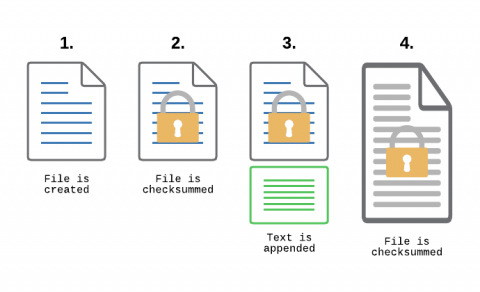
The Life of the Sysadmin: A Patch Tuesday Story
The System Administrator! AKA the Sysadmin. The keeper of the network, computers – well basically all things technology. The one who is hated for imposing complex passwords and other restrictions, but taken for granted when everything works well. They are the first to be called when “facebuuk.com” reports: “domain does not exist”.