Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Monitoring
Revealing Suspicious VPN Activity with Anomaly Detection
Application Monitoring with a Web Application Firewall (WAF) for Network Security
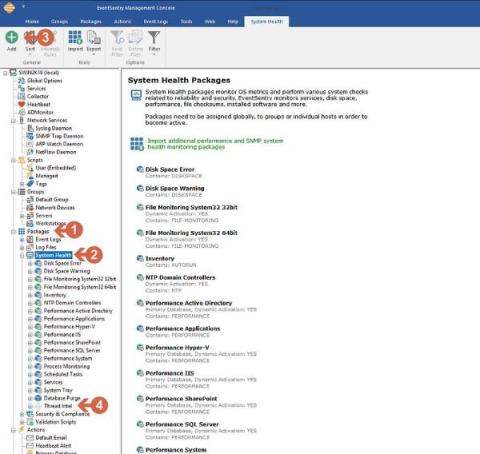
EventSentry Troubleshooting: Managing Database Size
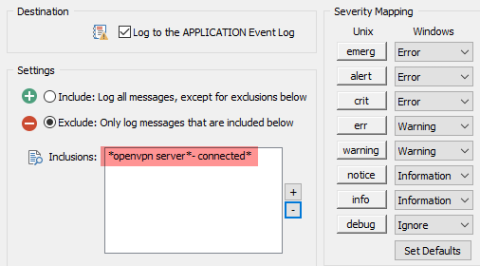
EventSentry Troubleshooting: Reducing the number of email notifications
Understanding the 4 Types of Network Monitoring Tools and Comparing Available Solutions
Today, IT networks are the backbone of nearly every business. Simply put, if your network isn’t performing at its best, the flow of data and services will be impeded, and your business operations will suffer. This modern reality makes effective server and network monitoring software not just a technical necessity but a business imperative.
Case Studies and Success Stories: Transforming Workplaces With Buddy Punch
Predict the Future! A universal approach to detecting malicious PowerShell activity
So, here’s the deal with AntiVirus software these days: It’s mostly playing catch-up with super-fast athletes — the malware guys. Traditional AV software is like old-school detectives who need a picture (or, in this case, a ‘signature’) of the bad guys to know who they’re chasing. The trouble is, these malware creators are quite sneaky — constantly changing their look and creating new disguises faster than AntiVirus can keep up with their photos.
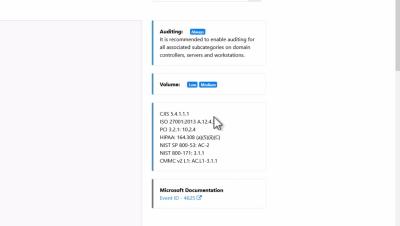
CMMC v2 Compliance with EventSentry
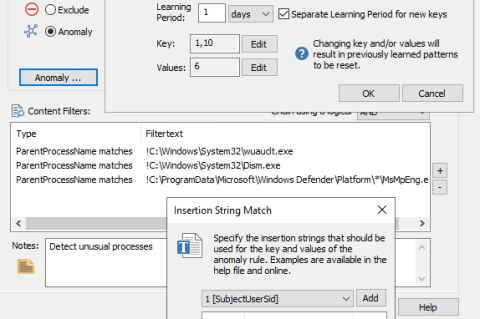
EventSentry v5.1: Anomaly Detection / Permission Inventory / Training Courses & More!
We’re extremely excited to announce the availability of the EventSentry v5.1, which will detect threats and suspicious behavior more effectively – while also providing users with additional reports and dashboards for CMMC and TISAX compliance. The usability of EventSentry was also improved across the board, making it easier to use, manage and maintain EventSentry on a day-by-day basis. We also released 60+ training videos to help you get started and take EventSentry to the next level.