Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
CI CD
It's Time to Get Hip to the SBOM
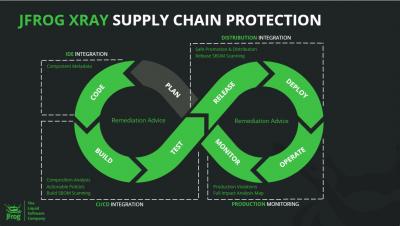
The DevOps, IT security and IT governance communities will remember 2021 as the year when the Software Bill of Materials , or SBOM, graduated from a “nice to have” to a “must have.” Around for years, the SBOM has now become a critical DevSecOps piece, which everyone must thoroughly understand and incorporate into their SDLC (Software Development Lifecycle).
Reflections on trusting plugins: Backdooring Jenkins builds
In this post we explore how an attacker who has compromised a Jenkins instance can backdoor software built with it and what security measures are critical to ensure protection against attacks.
How to protect your secrets with Spectral and JFrog Pipelines
Thousands of secrets leak daily on public git repositories, including over two million corporate secrets in 2020 alone. This can happen to anyone! For example, in January 2021, an Amazon cloud engineer accidentally committed almost a gigabyte worth of sensitive data that included their own personal documents, as well as passwords and cryptographic keys to various AWS environments on his personal GitHub repository.
Appknox - Highest rated mobile application security solution
Bring Xray Out of the Box with Dependency and Binary Scanning
Shifting left security means you, the developer, catching and fixing vulnerabilities and license violations early in the SDLC. That’s why Xray scans binaries pushed to Artifactory by your builds, and alerts you when there are issues with your dependencies. But catching them earlier, even before checking in code, can be important for developers shifting left.
JFrog detects malicious PyPI packages stealing credit cards and injecting code
Software package repositories are becoming a popular target for supply chain attacks. Recently, there has been news about malware attacks on popular repositories like npm, PyPI, and RubyGems. Developers are blindly trusting repositories and installing packages from these sources, assuming they are secure.