Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
CI CD
What's New with JFrog Xray and DevSecOps
As we look to improve the quality and capabilities of the JFrog DevOps Platform, especially in the world of DevSecOps, we have added powerful new features to further enhance the award-winning JFrog Xray. The capabilities detailed below cement Xray’s position as a universal software composition analysis (SCA) solution trusted by developers and DevSecOps teams globally to quickly and continuously identify open source software vulnerabilities and license compliance violations.
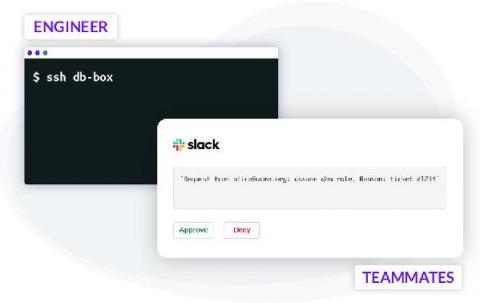
Pull Requests for Infrastructure Access
Making frequent changes to cloud applications running in production is the de-facto standard. To minimize errors, engineers use CI/CD automation, techniques like code reviews, green-blue deployments and others. Git pull requests often serve as a foundational component for triggering code reviews, Slack notifications, and subsequent automation such as testing and deployments. This automated process enforces peer reviews and creates enough visibility to minimize human error.
Automatically Assess and Remediate the SolarWinds Hack
With software supply chain attacks on the rise, are you wondering how you can recover quickly from the recent SolarWinds breach at your company? Months after its discovery, the devastating SolarWinds hack remains a top concern for business, government and IT leaders. This destructive supply chain attack put the spotlight on software development security — a critical issue for the DevOps community.
Scaling Software Supply Chains Securely
Software supply chains are mission-critical for digital businesses, and as global conditions accelerate the growth in contactless interactions and transactions, many organizations are reviewing how to solve the challenge of scaling the volume and velocity of their software development and release processes to meet the digital demand. The latest JFrog Platform release delivers a rich payload of new capabilities to scale and secure the software supply chain for digital businesses.
How to cyber security: Minimize risk and testing time with Intelligent Orchestration
Integrating AST tools into your CI/CD pipeline shouldn’t compromise your development velocity. Learn how Intelligent Orchestration can help. Sometimes it feels like software development is at the crux of the collision between an unstoppable force and an immovable object. The answer to putting security in every phase of development is partly process and partly automating and integrating security testing into the build and test phases of development.
How to set up Software Security and Compliance for Your Artifacts
The simplest way to ensure the safety of all the open source (OSS) components used by your teams and sites, is with a software composition analysis (SCA) tool. You need an automated and reliable way to manage and keep track of your open source usage. With JFrog Xray, you can set up vulnerability and license compliance scanning built into your software development lifecycle (SDLC).
Automate DAST in DevSecOps With JFrog and NeuraLegion
NeuraLegion’s VP Oliver Moradov takes us through how you can use JFrog and NeuraLegion to automate AppSec testing in your pipelines. The days of long release cycles are well and truly behind us — it is simply not feasible in our agile development world, with developers delivering software and more features at an unprecedented scale and speed. With DevOps, we have multiple development teams running multiple concurrent builds, which is great, but security testing has not kept up.
Yet Another Case for Using Exclude Patterns in Remote Repositories: Namespace Shadowing Attack
The npm Registry is vulnerable for supply chain impersonation attacks. Make sure you create npm scoped packages and force exclude patterns.
Rooting out the cybersecurity risk in your CI/CD pipeline
When it comes to productivity, agility, and efficiency - continuous integration/continuous delivery (CI/CD) pipelines are great. When it comes to ensuring cybersecurity, they leave a lot to be desired. In fact, and especially given the popularity of CI/CD pipelines now, securing continuous environments might turn into the most important security challenge of the next decade.