Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
Live Impact Analysis with Styra Load: How to Not Break Production
Failing Less at Kubernetes with Policy as Code & OPA
Kubernetes has become the de facto way to run modern computing platforms, both in the cloud and on-premise. This is a huge change from just a few years ago, and it didn’t happen overnight. On the road to production readiness with Kubernetes, many have run afoul. Thanks to Kubernetes Failure Stories though, engineering teams from around the world have shared in detail what they did wrong and how they can avoid making the same mistake in the future.
What is SOC 2 and how do you achieve SOC 2 compliance for containers and Kubernetes?
SOC 2 is a compliance standard for service organizations, developed by the American Institute of CPAs (AICPA), which specifies how organizations should manage customer data. SOC 2 is based on five overarching Trust Services Criteria (TSC): security, availability, processing integrity, confidentiality, and privacy. Specifically, the security criteria are broken down into nine sections called common criteria (CC).
Container security essentials
What Is Kubernetes Admission Control?
Kubernetes admission control is a mechanism that validates and modifies requests to the Kubernetes API server before they are processed. Admission control can enforce policies, security rules, resource limits, default values and other elements of the cluster’s use. This mechanism can also reject requests that violate certain rules or conditions.
Introducing Calico Runtime Threat Defense-The most extensive security coverage for containers and Kubernetes
Containerized applications are complex, which is why an effective container security strategy is difficult to design and execute. As digitalization continues to push applications and services to the cloud, bad actors’ attack techniques have also become more sophisticated, which further challenges container security solutions available on the market.
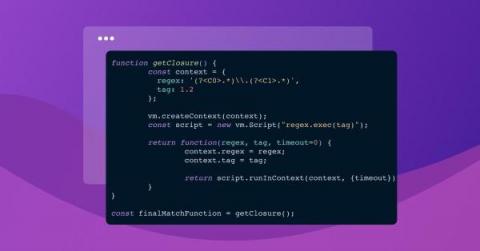
Timing out synchronous functions with regex
How hard can it be to support custom container image tags? Turns out… quite! I know this because my team has been busy at work on our new custom base image support for Snyk Container, andwe were tasked with the following problem: Given a tag, parse its parts to be able to compare it to other similar tags. It was a fun problem to solve, and we'd love to share how we got to our final solution!
Proxyjacking has Entered the Chat
Did you know that you can effortlessly make a small passive income by simply letting an application run on your home computers and mobile phones? It lets others (who pay a fee to a proxy service provider) borrow your Internet Protocol (IP) address for things like watching a YouTube video that isn’t available in their region, conducting unrestricted web scraping and surfing, or browsing dubious websites without attributing the activity to their own IP.
GitOps with Styra DAS and OPA
The practice of infrastructure as code (IaC) has enabled platform teams to control infrastructure using code stored in Git. This enables teams to apply standard development practices like code review and testing to infrastructure management. The practice of GitOps takes this a step further by: Open Policy Agent (OPA), thanks to its Rego policy language, enables organizations to manage their authorization policies as code (PaC).