Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
Overcoming Security Gaps with Active Vulnerability Management
Organizations can reduce security risks in containerized applications by actively managing vulnerabilities through scanning, automated image deployment, tracking runtime risk and deploying mitigating controls to reduce risk Kubernetes and containers have become de facto standards for cloud-native application development due to their ability to accelerate the pace of innovation and codify best practices for production deployments, but such acceleration can introduce risk if not operationalized properly.
How to avoid Kubernetes misconfigurations
Detect and Respond to Workload Threats
Securing Cloud, Containers, and Kubernetes
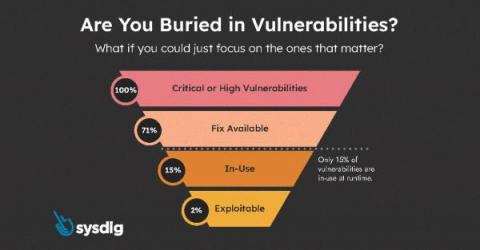
Run Faster, Runtime Followers
Recently, there has been a flurry of announcements claiming to have what we call Runtime Insights, the ability to prioritize vulnerabilities. Here are two examples: I can confirm that this approach works, and it works very well. It substantially decreases the number of vulnerabilities that a team has to manage, sometimes by a factor of 100 or more! How do I know it? Because Sysdig invented this approach.
Comparing Restic vs Kopia for Kubernetes Data Movement
When we began developing CloudCasa, a Software as a Service (SaaS) platform, for protecting Kubernetes applications, we looked at the data protection landscape and focused on areas that we could improve upon and give back to the user community. We wanted to provide them with a quick and efficient way in which they could start protecting this infrastructure with minimal effort, overhead, and most importantly minimal cost.
What you can't do with Kubernetes network policies (unless you use Calico)
Kubernetes documentation clearly defines what use cases you can achieve using Kubernetes network policies and what you can’t. You are probably familiar with the scope of network policies and how to use them to secure your workload from undesirable connections. Although it is possible to cover the basics with Kubernetes native network policies, there is a list of use cases that you cannot implement by just using these policies.
Using Calico Egress gateway and access controls to secure traffic
As more organizations embrace containerization and adopt Kubernetes, they reap the benefits of platform scalability, application portability, and optimized infrastructure utilization. However, with this shift comes a new set of security challenges related to enabling connectivity for applications in heterogeneous environments.
Reduce resolution time for container vulnerabilities with ServiceNow & Sysdig
Today, security and development teams are drowning in vulnerabilities. Most security tools identify issues, but don’t provide reliable prioritization or simplify remediation. To help solve these challenges, Sysdig runtime vulnerability management – part of Sysdig’s Cloud Native Application Protection Platform (CNAPP) – provides a runtime image scanner coupled with an eBPF probe to analyze container behavior and identify the vulnerable packages that are in use at runtime.