How security teams manage threat intelligence with Tines
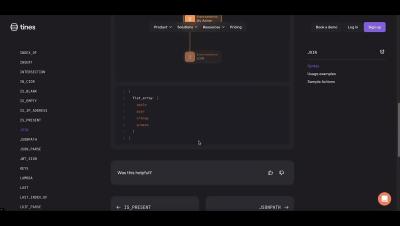
Every day, the growing threat landscape presents new challenges for security teams, with threats becoming more diverse and complex. But while teams typically have the tools to gather the intelligence they need, they often run into trouble with the next steps in the process - enriching, prioritizing and responding to this intel.