Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Blog
The Urgent Need For Cyber Resilience in Healthcare
A US hospital closed two years after a ransomware incident, highlighting that the health sector continues to be under threat.
Cyber Security Solutions For The Health Care Sector
In an era where digital data is integral to the efficient operation of the health care industry, the importance of robust cyber security solutions cannot be overstated. The sensitive nature of patient data combined with the industry’s increasing reliance on technology, significantly escalates the potential risks and consequences of cyber threats.
Account Takeover (ATO) Fraud: What Is It and How It Happens
The impacts of account takeover fraud are genuine. According to the Javelin 2022 Identity Fraud Study, 22% of U.S. adults have been victims of account takeover attacks. This type of fraud can have devastating financial and personal consequences when criminals gain access to accounts and exploit them for theft and abuse. Understanding account takeover and how it happens enables individuals and businesses to better detect and prevent these schemes.
PokerStars Suffers Serious Data Breach Exposing 110k People
PokerStars is one of the largest online poker rooms in the world and has millions of registered customers that use the platform to play remotely with others from different areas of the world. The company is well-known for providing poker and other card-game services and is part of a larger gambling network with more organizations. The company houses data for millions of users that access the platform, and some of that data was just accessed in a recent breach.
TrustCloud & VanRein Compliance Partner to Make Compliance Accessible and Affordable
TrustCloud is thrilled to announce a partnership with VanRein Compliance, a leading managed compliance provider that builds and manages clients’ compliance programs via audits, custom policies and procedures, online training, and more. TrustCloud and VanRein Compliance both share a mission – to make compliance accessible and affordable for all.
Honeypot Recon: New Variant of SkidMap Targeting Redis
Since Redis is becoming increasingly popular around the world, we decided to investigate attacks on the Redis instance. We didn’t have to wait long for the first results of the Honeypot. The trap caught an activity about which the Western world does not hear too often while analyzing SkidMap. More importantly, this variant turned out to be a new, improved, dangerous variation of the malware. Its level of sophistication surprised us quite a bit.
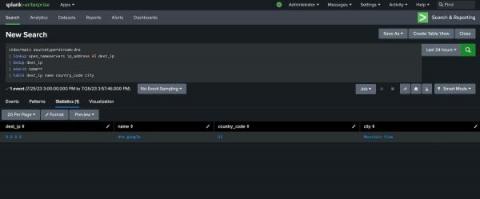
Using the Lookup Command for Threat Hunting (Lookup Before You Go-Go)
What is the SSL Not Available Risk?
5 ways to prevent phishing from ruining your summer vacation
During the summer months, when employees and customers are away on vacation, things usually slow down for businesses. But for cybercriminals, the opposite is true because they are busy taking advantage of minimal staffing levels in companies during the vacation period to launch complex attacks. The U.S. Federal Cybersecurity and Infrastructure Security Agency (CISA), warns that the risk of being hit by a cyberattacks rises over the holidays and summer vacation-themed phishing attacks gain momentum.