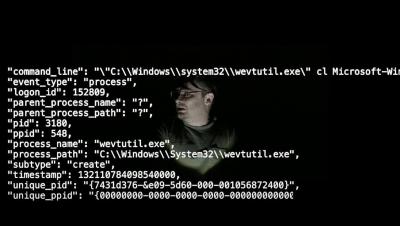
SOCtails - Unify Security Operations with Splunk Mission Control
Security teams constantly pivot between multiple tools and management consoles in order to detect, investigate, and respond to security incidents. It's time-consuming and complex. And it's Kevin's personal nightmare. Jeff shows Kevin how to unify his security operations across detection, investigation and response using Splunk Mission Control.