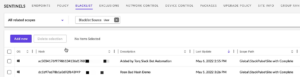
How Torq Remediates the 3CX Supply Chain Attack
By Dallas Young Sr. Technical Marketing Manager, Torq According to researchers, the 3CX Voice over Internet Protocol (VoIP) desktop program for Windows and MacOS, which boasts over 600,000 customers and 12m daily users, has been compromised by a DLL sideloading attack and used in several supply chain attacks. 3CX is a private branch exchange (PBX) system, a private telephone network used within a company or organization.