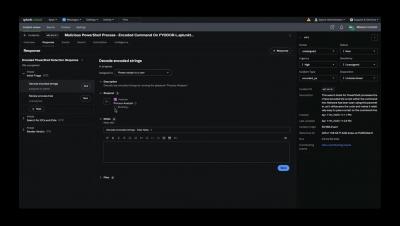
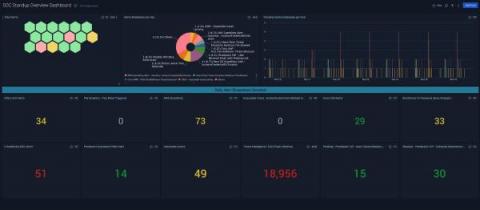
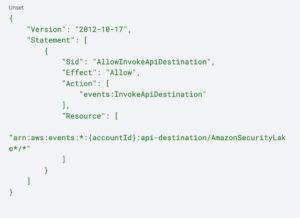
How Torq Hyperautomates Threat Hunting
Threat hunting is the process of proactively searching for hidden threats in an organization’s environment – a critical modern cybersecurity activity. However, relying on manual threat hunting alone can be time-consuming and resource-intensive.