Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
May 2023
Electronic Mailroom: Inadvertent Data Breaches
Turning Intelligence Into Action with Cybersixgill and Torq
The Top 4 Criteria for Choosing a Security Automation Solution
Arctic Wolf Short: Leveraging Holistic Visibility In An Unpredictable Threat Landscape
Do you Work in a SOC Noise Factory?
Gabrielle is a security engineer. She deploys tools to scan for threats and vulnerabilities, read logs, and manage the security risks for her company, but is all that data really helping? Sometimes, it seems like she works in a noise factory instead of a SOC. The cacophony of all the log and event data and vulnerability scans are pouring into the SIEM, and it’s Gabrielle’s job to listen to the symphony of data and find the out-of-tune notes.
Hype vs. Reality: Are Generative AI and Large Language Models the Next Cyberthreat?
SOC Metrics: Security Metrics & KPIs for Measuring SOC Success
Securing your enterprise: The importance of a security operations center
The world is increasingly embracing cloud technology. The fact that cloud requires minimal infrastructure and operational costs is attracting enterprises to shift to cloud. Remote and hybrid work modes following the pandemic has added to the continued rise of cloud.
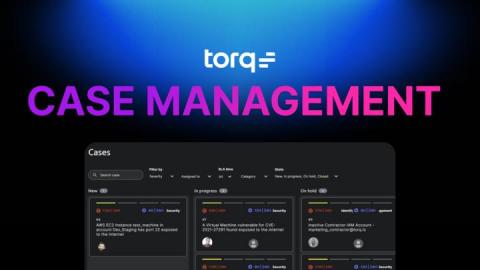
How Torq Hyperautomation Reinvents Security Case Management
Leveling Up Security Operations with Risk-Based Alerting
Using Co-Managed SOC to Derive Maximum Value from a SIEM Investment
Security information and event management (SIEM) systems are crucial to cyber security, providing a solution for collecting and analyzing alerts from all manner of security tools, network infrastructure, and applications. But simply having a SIEM is not enough because to be truly effective, it must be properly configured, managed, and monitored 24x7.