Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
October 2022
Arctic Wolf Managed Risk
What Security Teams Want from MDR Providers
Managed Detection and Response (MDR) Buyer's Guide
All organizations should have access to the skills needed to detect and contain threats. But, typically, only the very largest enterprises can afford the millions in annual staff and infrastructure investments required to maintain a Security Operations Center (SOC).
Critical Remote Code Execution Vulnerability in VMware Cloud Foundation NSX-V: CVE-2021-39144
How to Secure Funding from the Infrastructure Investment and Jobs Act: The Deadline Is Approaching
What Is MITRE D3FEND, and How Do You Use It?
MITRE is a world-renowned research organization that aims to help build a safer world. It is probably best known in the information security industry for being the organization behind the industry-standard CVE (Common Vulnerabilities and Exposures) list. Each entry on the list is supposed to include an explanation of how the vulnerability could be exploited. These attack vectors are tracked and defined in another well-known knowledge base called ATT&CK, which is also maintained by MITRE.
SOC Talent: How to Stay Competitive in the Hiring and Retention Game
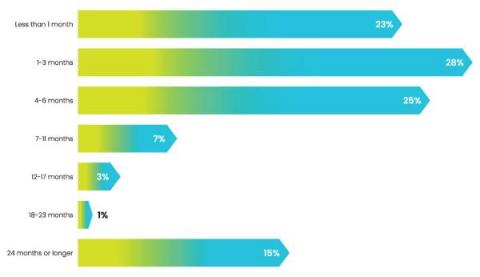
The disparities in some key areas in our 2022 Devo SOC Performance ReportTM provide clear evidence that the issues facing organizations since the start of the global pandemic in early 2020 continue to affect SOC performance, especially in the areas of hiring and retaining SOC talent.
What Is the SHIELD Act And How Do You Achieve Compliance?
Why You Need To Update Your Software | Cybersecurity Awareness Month
The Nightmare of Delayed Updates
Clickbait: Think Before You Click
Jason Chan on Harnessing Security Automation to Manage Cyberthreat Complexity
Torq is extremely proud to have Jason Chan on our advisory board. Jason has more than 20 years of experience working in cybersecurity. He’s one of the world’s leading experts in adopting security automation, cloud security, and enhancing security in modern software development practices. Jason’s most recent career experience was leading the information security organization at Netflix for more than a decade.
Why Auto Dealers Are Prime Targets for Ransomware Attacks
Paracyber Team: The Password
CVE-2022-40684: Widespread Exploitation of Critical Fortinet Authentication Bypass Vulnerability
Critical Remote Code Execution & Authentication Bypass Vulnerabilities in Aruba EdgeConnect Enterprise Orchestrator
Five tips for managing the cost of your security operations
With the global economy experiencing a slowdown, security teams are feeling the pressure to reduce costs without sacrificing security. But while it's important to be fiscally responsible, making cuts in the wrong areas can put your organization at risk. Malicious actors know that businesses are under even more pressure during times of economic turmoil.
Calculate the Cost of A Data Breach
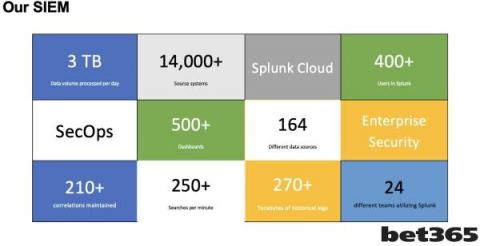
Inside the SecOps Team at bet365: Moving your SIEM to the Cloud
Hello, I love to look behind the scenes of SecOps teams to learn how they operate. Recently I had the pleasure to work with John Eccleshare, Head of Compliance and Information Security, at bet365 as John took the stage at Gartner Security and Risk Summit in London.
Security Basics: Incident Response and Automation
Incident response is one of the most challenging tasks that IT teams face. It's challenging not just because it typically involves many stakeholders and moving pieces, but also because teams usually face pressure to respond as quickly as possible. That's why investing in incident response automation is a wise choice. Although it may not be possible to automate every aspect of every incident response workflow, being able to automate at least the major elements of incident response will yield incident management processes that are faster, more reliable, and more consistent.Keep reading to learn about the components of incident response and which incident response activities to start automating.
CVE-2022-40684: Critical Remote Authentication Bypass Vulnerability in FortiOS & FortiProxy
Help Protect Seniors from Cyber Crime
Threat Intelligence 101
Cybersecurity Awareness Month: Why You Need To Use Strong Passwords
Updated Guidance for Microsoft Exchange Zero-Day Vulnerabilities Exploited in the Wild
Additional Updated Guidance for Microsoft Exchange Zero-Day Vulnerabilities Exploited in the Wild
Keeping Your Organization Secure with Limited SOC Resources
Organizations face a growing threat from cybercriminals while struggling to find qualified security professionals who can protect their infrastructure and sensitive data. This blog will explore the concept of a Security Operations Center (SOC) and the role of SOC analysts in securing your organization. We will also discuss how your organization can leverage automation to improve SOC effectiveness and fill in the gaps when you cannot support a full staff of security professionals.