SIEM in Seconds - Streamline Investigations with Splunk Enterprise Security
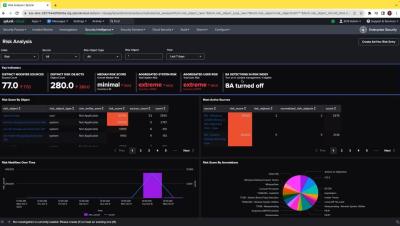
A SOC analyst's day-to-day tasks involve investigating notable events to gather information about security incidents. Recent enhancements within the Incident Review and Risk Analysis dashboards in Splunk Enterprise Security allows analysts to streamline their investigation process and reduce the number of manual tasks they perform daily. Multiple drill-down searches on correlation rules, updates to "dispositions" in the Incident Review dashboard, and hyperlinks in Correlation Search “Next Steps” allow for faster, more efficient investigations.