Coverity - Static Analysis by Synopsys
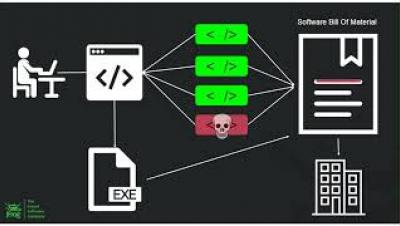
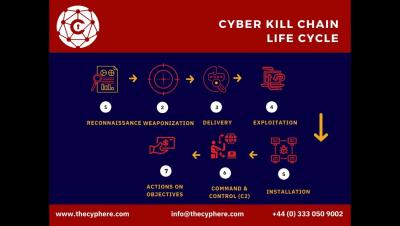
Coverity, is the static analysis solution with over 15 years of experience scanning tens of thousands of applications. Coverity is a market leader in application security and embedded applications. It’s the only SAST solution that combines best-in-class security and software code quality in a single product.