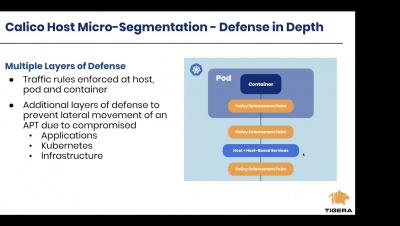
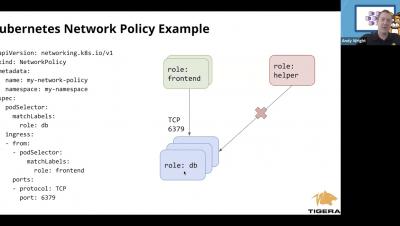
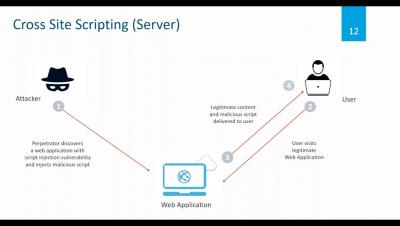
Getting up and running with Calico Host Micro segmentation Protection on AWS
In this online training, we will explain how to install and configure Calico on a vm/host to apply network policy to resources outside your K8s cluster. The talk will be primarily a walkthrough and demo and you will receive all manifests and instructions to do the demo on your own after the session.