Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Lessons Learned Deploying Corelight in the Black Hat Asia NOC
Last month, Corelight had the distinct privilege of joining Cisco, NetWitness, Palo Alto Networks, Arista, and our internet service provider, MyRepublic, to provide availability and network security overwatch to the Black Hat Asia network in Singapore. This marked our first appearance in the Black Hat Network Operations Center (NOC).
Look both ways: Preventing suspicious behavior with end-to-end detections
In the rapidly evolving digital landscape, malicious actors constantly adapt their strategies to infiltrate our systems. Traditional endpoint detection mechanisms are no longer sufficient to protect our applications and workloads against advanced threats. To effectively address this concern, it has become imperative to embrace a broader approach to threat detection. This entails a paradigm shift towards incorporating both agent-based and agentless detection methods.
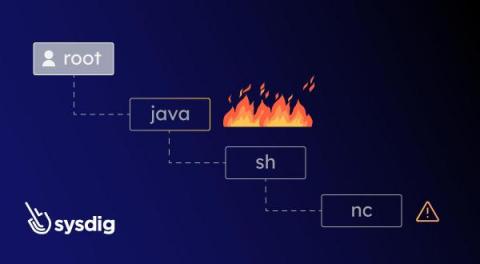
Sysdig Enriched Process Trees, an Innovative Approach to Threat Detection
Discover how Sysdig Secure’s new Process Tree feature improves threat investigation. Imagine you’re investigating a security related detection, the investigation was triggered by the execution of stat/etc/shadow in one of your containers. Is this a sign of a legitimate activity, such as a developer debugging an app, or a sign that your container has been compromised? It depends on the context.
Stop Cloud Breaches in Real Time and Accelerate Investigation and Response with Sysdig CDR
Is your organization grappling with the relentless pace of ever-changing threats in the cloud? Are you spending hours investigating security events without identifying the root cause of the problem?
3 Reasons to Leverage AI for Enhanced Threat and Vulnerability Management
As the cyber threat landscape continues to evolve, you know there’s a growing need to ensure applications and software are protected from malicious actors. A holistic and intelligent approach to threat and vulnerability management is essential for ensuring security against modern cyber risk. By leveraging AI-powered tools, especially for tasks like remediating security flaws, you can manage and reduce risk quickly and effectively.
Celebrating CrowdStrike's New Network Detection Service "Powered by Corelight"
Several months ago, we announced that our strategic alliance partner CrowdStrike decided to use our Open NDR technology across its professional services portfolio. This wasn’t just a meaningful validation for us—it was also a testament to the importance CrowdStrike places in arming its world-class Services teams with the technology that can best ensure the protection of its customers.
Microsoft threat detection and response: five key pitfalls (and how to address them)
Threat hunting 101: Leveraging MITRE ATT&CK framework for extended threat detection
Threat detection and mitigation is one of the core responsibilities of a SOC. With cyberattacks becoming more sophisticated, it has become arduous for security analysts to secure their network from threats. Hybrid work and BYOD policies are making it more difficult for SOCs to keep track of network activities. Attackers continue to improvise new tactics and techniques to compromise an organization’s network.
Why Cyber Threat Detection and Response Is So Hard
Breakthrough innovation arises primarily in response to two conditions. One, when new technology emerges that creates new demand by fulfilling needs customers didn’t know they had. Think smartphones. A generation ago, people didn’t know they needed to be tethered to a phone the size of their palm that was also a camera, a bank, an encyclopedia and a shopping mall. Two, when new challenges arise that require innovation to address them.