Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
The Essential Guide to Understanding the DevOps Lifecycle
DevOps has revolutionized how software is developed and deployed by introducing a more collaborative environment for development and bridging the gap between developers and operations. All the while ensuring flexibility to meet any consumer or market demands. However, it would be best if you implemented a proper DevOps lifecycle in your organization to take full advantage of all the benefits offered by DevOps.
The Essential Guide to Understanding the DevOps Lifecycle
DevOps has revolutionized how software is developed and deployed by introducing a more collaborative environment for development and bridging the gap between developers and operations. All the while ensuring flexibility to meet any consumer or market demands. However, it would be best if you implemented a proper DevOps lifecycle in your organization to take full advantage of all the benefits offered by DevOps.
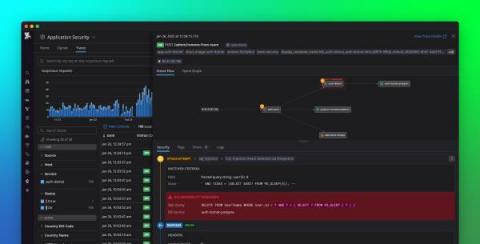
Introducing Datadog Application Security
Securing modern-day production systems is expensive and complex. Teams often need to implement extensive measures, such as secure coding practices, security testing, periodic vulnerability scans and penetration tests, and protections at the network edge. Even when organizations have the resources to deploy these solutions, they still struggle to keep pace with software teams, especially as they accelerate their release cycles and migrate to distributed systems and microservices.
Enterprise security: Digital transformation and risk management with Anheuser-Busch Inbev and Manulife
As enterprises continue to undergo digital transformation, rapidly delivering secure software has become a necessity. Essential to this goal is the ability to measure and manage application risk across a large number of projects and development teams. In this post, we’ll cover two insightful talks from SnykCon 2021 about risk management and measuring key risk indicators for enterprise applications.
Vulns Unleashed: Pwnkit
How To Set Up SSH Keys
At Teleport, we advocate SSH certificates over SSH keys and passwords as the best authentication method for SSH. Nothing beats the security and operational flexibility of using certificate-based authentication for a large fleet of SSH servers running on dynamic infrastructure. But in practice, certificate-based authentication is far from the de facto authentication method, and sometimes we may need to use SSH keys.
Fun with ciphers in copycat Wordles
Here at Snyk, we spend a lot of time researching vulnerabilities. We do that because there are a lot of other folks out there researching new ways to break into apps and systems. We’re often putting on our “grey hats” to think like a malicious hacker. I regularly view-source, look at network traffic and eyeball query strings. One such delicious little query string caught my attention this week on one of the many copycat Wordle sites.
A Malicious Package Found Stealing AWS AIM data on npm has Similarities To Capital One Hack
In the latter part of December 2021, WhiteSource Diffend detected the new release of a package called @maui-mf/app-auth. This package used a vector of attack that was similar to the server side request forgery (SSRF) attack against Capital One in 2019, in which a server was tricked into executing commands on behalf of a remote user, thereby enabling the user to treat the server as a proxy for requests and gain access to non-public endpoints.