Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
opsdemon
Latest posts
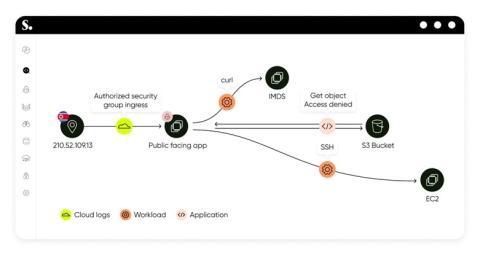
Sweet Security Introduces Evolutionary Leap in Cloud Detection and Response, Releasing First Unified Detection & Response Platform
Sweet Security Introduces Evolutionary Leap in Cloud Detection and Response, Releasing First Unified Detection & Response Platform. With Sweet, customers can now unify detection and response for applications, workloads, and cloud infrastructure.
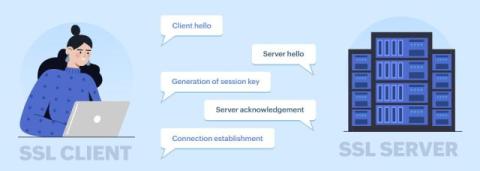
What is a Secure Socket Layer (SSL)? How does it ensure safe connection?
Imagine all your online activity being put out in the open—as private as a billboard in Times Square. Before SSL, your private internet information was vulnerable to exposure. However, with the advent of SSL, encryption became part of how the data was transferred between web browsers and servers, ensuring privacy and security. SSL transforms regular HTTP into the more secure HTTPS, safeguarding your online activities.
Trustwave's 2025 Cybersecurity Predictions: AI as Powerful Ally for Cyber Defenders and Law Enforcement
As 2024 comes to a close, we went around the room and asked some of Trustwave’s top executives what cybersecurity issues and technology they saw playing a prominent role in 2025. Over the next several weeks their thoughts will be posted here, so please read on and stay tuned! As we approach 2025, cybersecurity landscapes are set to evolve in unprecedented ways, with artificial intelligence (AI) taking center stage for both cyber defenders and threat actors alike.
5 steps of the security questionnaire process to automate today
As organizations sell to more discerning buyers, scrutiny on security and compliance practices grows. It’s certainly warranted—the frequency of third-party breaches is on the rise. In our State of Trust Report, almost half of all organizations surveyed say that a vendor of theirs experienced a data breach since they started working together.
Keeper Rolls Out Expanded iOS Security Key Support and Enhanced 2FA Settings
Keeper is excited to announce two significant updates to our iOS app: support for USB-C plug-in hardware security keys and a new Two-Factor Authentication (2FA) frequency setting. These updates reflect our commitment to providing industry-leading security solutions while ensuring a seamless user experience. Continue reading to learn more about these updates and how you can try them out yourself.
Quick Learn: The Three Most Common Complaints in Access Management
We recently started a new blog series featuring our CEO and co-founder Rom Carmel. In this series, we discuss real issues from the field. So, check out what Rom Carmel has to say about the three complaints he hears the most in access management.
How Growing MSSPs Benefit from Tools with Public-Cloud Pricing
This blog was originally published on MSSP Alert on October 16, 2024. MSSPs want to grow—but the complexity of modern security operations (SecOps) and the unique demands of the security services market make this challenging. In this post, we’ll look at how tools with public cloud or public cloud-like pricing—pricing that is usage- or consumption-based rather than fixed fee or license-based—can help MSSPs grow more effectively and efficiently.
The Hidden Dangers of Legacy PAM: Why Your Security Solution May Actually Be a Risk
As a former federal CISO who has spent decades designing and securing enterprise infrastructure, I’ve grown increasingly concerned as organizations continue to rely on legacy Privileged Access Management (PAM) solutions designed for a different era. These systems, once the gold standard in security, have become dangerous liabilities in today’s modern cloud-native world.
Cyber Threat Hunting Explained: Advanced Techniques, Tools, and Intelligence
Explore Our Latest Insights on Artificial Intelligence (AI). Learn More.
The Human Factor: Why Most Cyber Breaches Start with People
68% of breaches involve a human element, with phishing leading the charge. Discover why promoting a security-conscious culture is critical for mitigating cyber risks.