Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Detection
Avoiding a false sense of security
Network Detection and Incident Response with Open Source Tools
What Security Teams Want from MDR Providers
Managed Detection and Response (MDR) Buyer's Guide
All organizations should have access to the skills needed to detect and contain threats. But, typically, only the very largest enterprises can afford the millions in annual staff and infrastructure investments required to maintain a Security Operations Center (SOC).
From Data to Deployment: How Human Expertise Maximizes Detection Efficacy Across the Machine Learning Lifecycle
Security is a data problem. One of the most touted benefits of artificial intelligence (AI) and machine learning (ML) is the speed at which they can analyze potentially millions of events and derive patterns out of terabytes of files. Computational technology has progressed to the point where computers can process data millions of times faster than a human could.
Improve Response in the Threat Detection Response Equation - Webinar
"Easy" button for cloud NDR visibility
As organizations continue to rapidly adopt cloud services, they struggle to expand network detection and response (NDR) capabilities to their hybrid and multi-cloud environments. Network visibility is critical for security operations center (SOC) teams to secure their cloud environments and ensure they can elevate threat detection and incident investigation capabilities. However, traditional NDR solutions require management, configuration and often lack the security context needed.
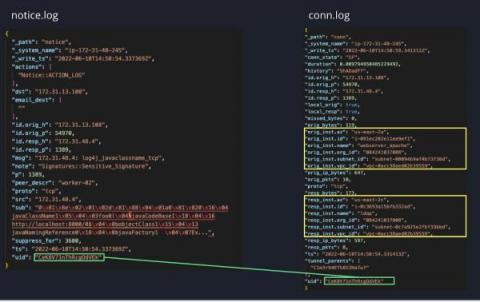
How to Reduce False Positives in Data Leak Detection - UpGuard
According to a 2021 study by UpGuard, over 51% of analyzed Fortune 500 companies were unknowingly leaking sensitive metadata in public documents - data leaks that could be very useful in a reconnaissance campaign preceding a major data breach. Without timely detection solutions, all corporate (and personal) accounts impacted by data leaks are at a critical risk of compromise, which also places any associated private internal networks at a high risk of unauthorized access and sensitive data theft.
BOD 23-01: Better visibility to reduce risk
“Knowing what’s on your network is the first step for any organization to reduce risk.” -CISA Director, Jen Easterly. On October 3, the Cybersecurity and Infrastructure Security Agency (CISA) issued Binding Operational Directive (BOD) 23-01: Improving Asset Visibility and Vulnerability Detection on Federal Networks.