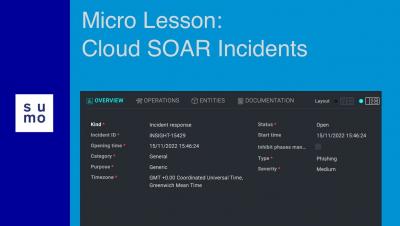
PyPi Malware Stealing Discord and Roblox Payment Info
In this livestream we dive into the latest set of malicious packages discovered by the Snyk security research team. We are joined by senior security researcher at Snyk Raul Onitza-Klugman as we also discuss how these findings came to be, what they mean for open source security, and some hypotheses about the future of supply chain security. Didn't catch the live stream? Ask all of your Snyk questions and we’ll do our very best to answer them in the comment section.