Rubrik and GraphQL - Episode 2 - GraphQL Queries
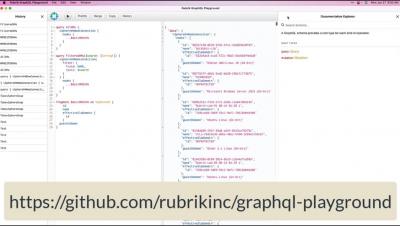
At the core of GraphQL lies the query. Queries allow us to fetch exactly the data we need from the Rubrik platform. This episode will dive into how we form basic queries to retrieve Rubrik objects for usage with automation. We’ll talk about how to form a query, create fragments, and pass data into our queries using variables.