Outpost24 webinar - Protecting Cezanne HR's cloud web application with continuous assessment
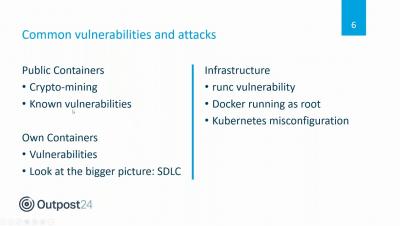
Cyberattacks like payroll scams and recruitment fraud are finding their way into organizations via HR which makes protecting your employee data just as important as customer data. Find out how Cezanne HR secure their SaaS application with continuous assessment to help their customers protect employee data. The Cezanne HR SaaS application is used by over 650 organizations across the globe to simplify human resource management. But when it comes to sensitive employee data, customers demand proof of security and need to know that their data is in safe hands. In this webinar John Hixon, R&D Director at Cezanne HR, will share in-depth insights into how he leverages manual pen testing and dynamic application security testing throughout the Software Development Lifecycle (SDLC) to uncover hidden risks in the application and protect their customer data. Join our host Simon Roe, Application Security Product Manager, and John as they discuss the importance of data protection in HR, and how this hybrid continuous assessment approach has helped them secure their business critical apps and maintain ISO certification standards at scale.