Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Outpost 24
Conveniently insecure: the tradeoff between security and convenience
When it comes to making business decisions about new technologies and software adoption into your organization – it’s vital to work with your security team to balance the need for speed without sacrificing security.
CISA Shields Up: How to prepare for the Russia-Ukraine cybersecurity hazard
CISA issues ‘Shields Up’ alert to warn US companies about potential Russian hacking attempts to disrupt essential services and critical infrastructure as the Russia-Ukraine crisis escalates. Get ahead of the situation with essential information.
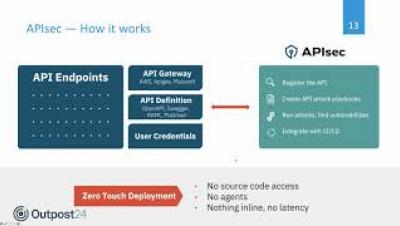
Outpost24 Webinar - API security 101 and how to secure your web applications
Product demo - Risk based vulnerability management Farsight
2022 Cybersecurity Predictions
2021 was the year businesses continued to adapt to new working patterns, digital transformation and battle the increasing threats from ransomware attacks. Here our panel of security experts share their predictions for the key security challenges and trends to look out for in 2022 ensuring you can beat the hackers at their own game.
Using Mitre Att&CK with threat intelligence to improve Vulnerability Management
Threat actors are constantly evolving their tactics and techniques in the attack lifecycle and infiltrate company infrastructure. While most organizations are already performing vulnerability management based on CVEs by MITRE, few have considered the powerful correlations between threat intelligence, CVEs and the ATT&CK® framework. In this blog we highlight the benefits of bringing them together to drive focused remediation and improve cyber defense.
Outpost24 acquires Specops for enhanced user security and secures further funding to continue growth
Alice in Windowsland: 3 ways to escalate privileges and steal credentials
Read how our red team used different attack techniques to hack AppLocker restrictions by implementing escalated privileges and reusing the Credentials Manager to extract stored data and Azure information.
OWASP Top 10 2021 is out - what's new and changed
It doesn’t seem that long ago that I wrote about the OWASP Top 10 changes that came in 2017. OWASP has announced the release for the new 2021 Top 10. Find out more about Broken Access Control and Cryptographic Failure vulnerabilities and understand what it means for application development and DevSecOps