Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Supply Chain
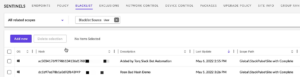
How Torq Remediates the 3CX Supply Chain Attack
By Dallas Young Sr. Technical Marketing Manager, Torq According to researchers, the 3CX Voice over Internet Protocol (VoIP) desktop program for Windows and MacOS, which boasts over 600,000 customers and 12m daily users, has been compromised by a DLL sideloading attack and used in several supply chain attacks. 3CX is a private branch exchange (PBX) system, a private telephone network used within a company or organization.
What You Need to Know About the 3CX Supply Chain Attack
Supply Chain Attack Targeting 3CX Softphone Application
Securing the web (forward)
We have grown to expect a reasonable level of privacy and security when we use services on the web and web-based applications. That’s because these services deal with every aspect of our daily lives — from money and finances, to how we interact with government services, to our education or the education of our children, to communicating with friends and family, to healthcare, to simply buying food to eat.
PulseMeter Report: Software supply chains
The not-so-distant memories of security events like Log4Shell and the SolarWinds attack keep software supply chain attacks front of mind for developers. There are things organizations can do to detect and deter malicious supply chain attacks, including the recently mandated (as per the U.S. federal government) software bill of materials (SBOM).
Coffee with Jim - Securing Against Supply Chain Cyber Attacks
Building a Secure Future: Strategies for Managing Cybersecurity in the Supply Chain
According to recent research, 68% of computer applications use open-source software libraries without the knowledge of the company. Another study by Argon Security shows that the supply chain attacks have grown up to 300% in 2021 compared to 2020.
Supply Chain Attacks: What You Need to Know
Third party Cybersecurity risks in securing the supply chain
Some of the biggest prevailing challenges in the cybersecurity world over the last year have been those revolving around securing the software supply chain across the enterprise. The software that enterprises build for internal use and external consumption by their customers is increasingly made up of third-party components and code that can put applications at risk if they aren't properly secured.