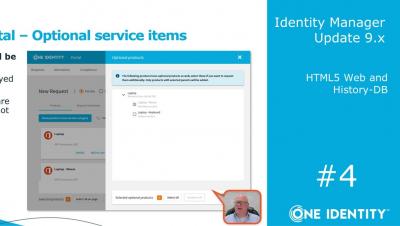
Why you need Active Roles, even if you have IGA
Here are two scenarios I come across frequently, with customers of all sizes, in all industries, when discussing One Identity Active Roles: These situations come from customers on all points of the "Identity Security Maturity" spectrum. Those who have nothing in place or some things in place or an entire stack of fully implemented solutions in every category.